Achievement:
Analyzing the logs of even the smallest Information Technology (IT) system can be a challenge, considering that they can generate millions of lines of log data in a very short time. Splunk® Enterprise is an industry leading tool that allows analysis of log data, which can enhance troubleshooting capability, improve system performance, and improve the security posture of an IT system.
Ivanti Connect Secure© (ICS) is a market-leading platform powered by the Ivanti Secure Socket Layer Virtual Private Network (SSL VPN) appliance, providing an architecture for secure access to and protection of network resources.
This is an approach for using Splunk Enterprise search capabilities to perform advanced data analysis of ICS logs. The advanced data analysis includes Splunk search pipelines that provide the following information:
- User session duration
- Concurrent active user sessions
- Application page load duration
Significance and Impact:
Splunk Enterprise is a platform for collecting, indexing, and analyzing enterprise data. Splunk can collect data from a host either through the Splunk Universal Forwarder or through the Syslog Configuration.
- The Splunk Universal Forwarder is a special version of Splunk Enterprise that runs as a process or service on the host and sends data to a Splunk Enterprise Server. It is the most common means of sending data to a Splunk server.
- Syslog is an industry standard for sending and receiving data and was developed as part of the Sendmail project in the 1980s. Splunk Enterprise can serve as a Syslog server, allowing a device or service to send data directly to the Splunk server datastore using User Datagram Protocol (UDP) or Transmission Control Protocol (TCP) on port 514. For the advanced data analysis presented in Research Details, the Syslog method is used to send data from ICS to the Splunk server.
- Once received by the Splunk server and added to the Splunk Enterprise Datastore, the log data is indexed so that it can be analyzed. For the advanced data analysis, regular expressions are used for field extraction, which is the process for giving structure to the unstructured logs sent to Splunk. Splunk searches are run against this indexed, semi-structured data.
Research Details:
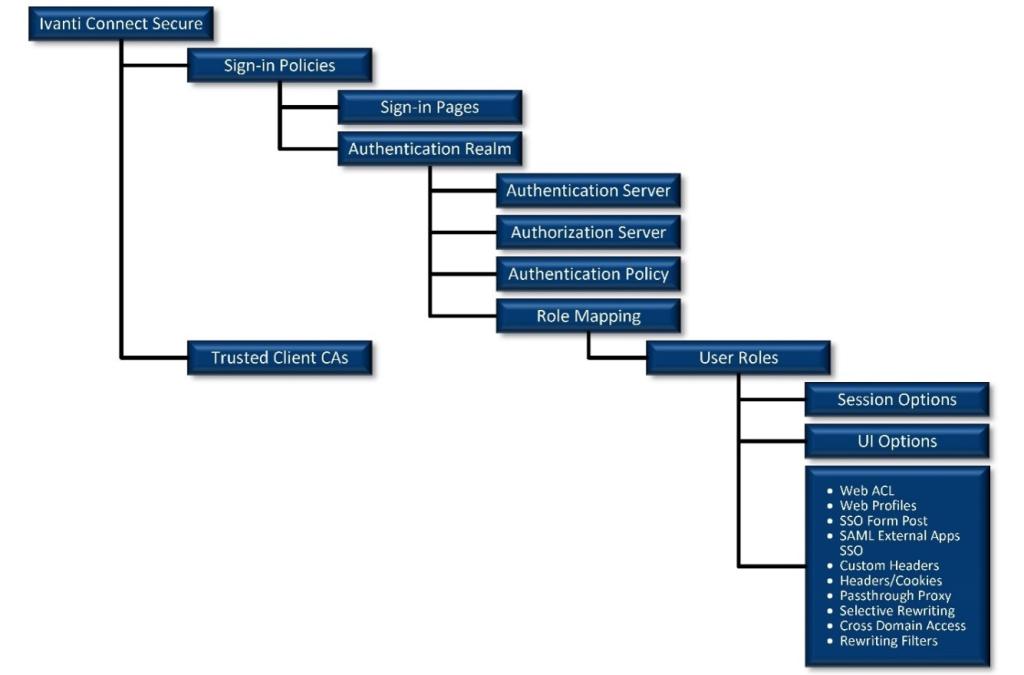
Ivanti Connect Secure
ICS (formerly Pulse Connect Secure) is a platform that runs on the Ivanti SSL VPN appliance and provides an architecture for secure access to and protection of network resources. Its ability to customize the format of log output, along with the ability to send the logs to a Syslog server, are important features for the advanced analysis capabilities presented.
- The ICS architecture provides a layered system of access controls, ensuring that internal resources are protected from unauthorized access.
- ICS utilizes custom filters for formatting log output. This feature is important as it makes it easier to extract fields from the raw log data once it is sent to the Splunk server datastore.
- ICS also can send log data directly to a Syslog server. An example configuration could send log data to a Splunk server, using a custom filter and the UDP transmission protocol.
Splunk Search
Splunk Enterprise provides a web interface that can be used to search and analyze the data that is collected. The search results are returned in an unmodified (i.e., raw) format. Splunk commands, along with field extractions, can be used to transform the raw data into charts, graphs, and tables. The searches also can be saved as reports, alerts, and dashboards for later use.
A Splunk search pipeline is a search that consists of several individual search commands that are connected using the “|” (pipe) character.
As data is sent to the Splunk server datastore, and then indexed, it is preprocessed to extract field-level information from the raw log data. For example, if a log entry contains user=[john.doe], then the Splunk indexer will automatically create a field called user and generate metadata to extract the same information from similar log entries.
Advanced Data Analysis
With a basic understanding of Splunk Enterprise and ICS, the advanced analysis of the ICS log data can readily be performed. Search pipelines can be used to complete the following advanced data analysis scenarios:
- User Session Duration – The length of an ICS user session from time of logon until the session ends by either logout, idle timeout, or maximum session length timeout.
- Concurrent Active User Sessions – The number of active user sessions each time a new user session is created.
- Application Page Load Duration – The amount of time it takes for an application page to load.
PI and affiliation: Brad Nance, ORNL, Performance Engineering Group Lead
Team: Brad Nance (Performance Engineering Group Lead)
Citation and DOI:
- Nance, Brad. Using Splunk® Enterprise Search Commands for Advanced Analysis of Ivanti Connect Secure© Logs. United States: N. p., 2022. Web. doi:10.2172/1872843.
Summary:
Splunk Enterprise is a powerful tool for analyzing log data. With a little effort to understand how it works and its capabilities, it can be used to perform advanced data analysis of ICS log data, resulting in enhanced troubleshooting capabilities, improved performance, and an improved security posture for an IT system.

