Achievement: A multidisciplinary team of researchers from Oak Ridge National Laboratory (ORNL) propose a forensic framework to decide if recorded controller area network (CAN) traffic, a de facto automobile communication standard, contains masquerade attacks. The proposed framework works at the signal-level and leverages time series clustering similarity to arrive at statistical conclusions. In doing so, we use available and readable signal-level CAN traffic in benign and attack conditions to test our framework. The results obtained from our evaluation demonstrate the capability of the proposed framework to detect masquerade attacks in previously recorded CAN traffic with high accuracy.
Significance and Impact: This work proposes a statistical forensic framework to detect masquerade attacks in the CAN bus. We quantify the empirical distribution of similarities of time series captures in benign and attack conditions. To accomplish this, we cluster time series using agglomerative hierarchical clustering (AHC) and compute the similarity between their corresponding dendrograms. We find that masquerade attacks can be detected effectively using the proposed framework, and its discriminatory power depends on the linkage function being used in the AHC as well as the the impact of the attacks on correlated signals. These results suggest that the proposed framework is a viable approach for detecting masquerade attacks in a forensic setting. We assume that the time series signal translation (or at least a high-fidelity translation) is readily available for use. This seems feasible with current and upcoming work in reverse engineering CAN bus signals.
The proposed framework detects all masquerade attacks in the ROAD dataset when the Ward linkage is used. We show that Ward’s linkage is an appropriate choice in this context because it tends to produce dense-enough clusters and enables the capture of meaningful changes in clustering assignations when attacks occur. In contrast, for the single linkage, clusters of signals tend to be spread out and often not compact enough with clusters having disparate elements. In the complete linkage, clusters of signals tend to be compact, but not far enough apart, with clusters having similar members. Additionally, for the average linkage, clusters tend to be relatively compact and relatively far apart, which strikes a balance between single and complete linkages.
We note that the detection performance may also depend on specific attack features. Here, the detection difficulty is based on the potential number of correlated signals that are affected by the attack. Thus, an attack scenario in which wheel speed signals are modified, such as in the correlated attack, has a more noticeable effect of disrupting correlation with other signals than an attack that modifies the reverse lights because the wheel speed correlation attack manipulates four highly correlated signals (and seemingly strong correlations to many other signals), whereas the reverse light attacks modify a single signal that has correlation with gear selection but not many other signals.
To the best of our knowledge, the results from this research are the first to show systemic evidence of a forensic framework successfully detecting masquerade attacks based on time series clustering using a dataset of realistic and verified masquerade attacks.
Research Details
- We detail a CAN forensic framework based on time series clustering similarity for detecting masquerade attacks. The proposed framework is based on (1) clustering time series using AHC; (2) computing a clustering similarity; and (3) performing hypothesis testing using the clustering similarity distributions to decide between benign and attack conditions.
- We perform a sensitivity analysis of detection capabilities with respect to the type of AHC used. We report our results and offer possible explanations.
- We evaluate the proposed framework on masquerade attacks from the ROAD dataset. Evaluation results show very high effectiveness of detecting attacks of different levels of sophistication. Our results indicate that the proposed forensic framework can be built upon to yield a viable real-time IDS.
Facility: This research used resources of the Compute and Data Environment for Science at ORNL. Real-world attack datasets were generated at the National Transportation Research Center at ORNL.
Sponsor/Funding: DOE ASCR
PI and affiliation: Michael D. Iannacone, Energy and Control Systems Security Group, Cyber Resilience and Intelligence Division, ORNL
Team: Pablo Moriano, Robert A. Bridges, Michael D. Iannacone (ORNL)
Citation and DOI: Pablo Moriano, Robert A. Bridges, Michael D. Iannacone, “Detecting CAN Masquerade Attacks with Signal Clustering Similarity”, Proceedings of the Fourth ISOC NDSS International Workshop on Automative and Autonomous Vehicle Security Workshop (Autosec), 2022, DOI: https://doi.org/10.14722/autosec.2022.23028
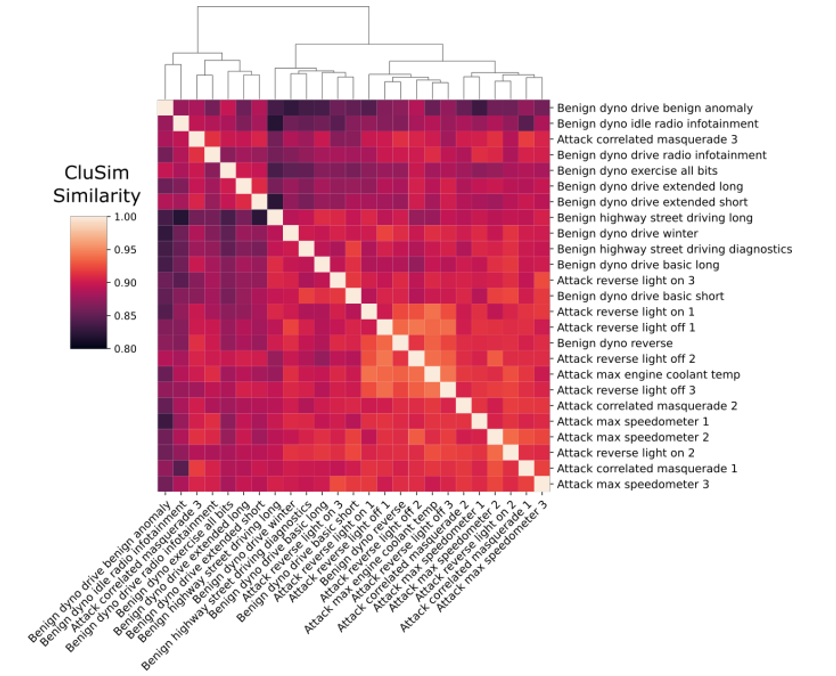
Summary: Vehicular Controller Area Networks (CANs) are susceptible to cyber attacks of different levels of sophistication. Fabrication attacks are the easiest to administer—an adversary simply sends (extra) frames on a CAN—but also the easiest to detect because they disrupt frame frequency. To overcome timebased detection methods, adversaries must administer masquerade attacks by sending frames in lieu of (and therefore at the expected time of) benign frames but with malicious payloads. Research efforts have proven that CAN attacks, and masquerade attacks in particular, can affect vehicle functionality. Examples include causing unintended acceleration, deactivation of vehicle’s brakes, as well as steering the vehicle. We hypothesize that masquerade attacks modify the nuanced correlations of CAN signal time series and how they cluster together. Therefore, changes in cluster assignments should indicate anomalous behavior. We confirm this hypothesis by leveraging our previously developed capability for reverse engineering CAN signals (i.e., CAN-D [Controller Area Network Decoder]) and focus on advancing the state of the art for detecting masquerade attacks by analyzing time series extracted from raw CAN frames. Specifically, we demonstrate that masquerade attacks can be detected by computing time series clustering similarity using hierarchical clustering on the vehicle’s CAN signals (time series) and comparing the clustering similarity across CAN captures with and without attacks. We test our approach in a previously collected CAN dataset with masquerade attacks (i.e., the ROAD dataset) and develop a forensic tool as a proof of concept to demonstrate the potential of the proposed approach for detecting CAN masquerade attacks.




