Filter News
Area of Research
News Topics
- (-) Cybersecurity (35)
- 3-D Printing/Advanced Manufacturing (116)
- Advanced Reactors (32)
- Artificial Intelligence (81)
- Big Data (49)
- Bioenergy (86)
- Biology (93)
- Biomedical (56)
- Biotechnology (20)
- Buildings (54)
- Chemical Sciences (55)
- Clean Water (29)
- Climate Change (91)
- Composites (25)
- Computer Science (181)
- Coronavirus (46)
- Critical Materials (23)
- Decarbonization (71)
- Education (3)
- Element Discovery (1)
- Emergency (2)
- Energy Storage (106)
- Environment (188)
- Exascale Computing (34)
- Fossil Energy (4)
- Frontier (38)
- Fusion (51)
- Grid (59)
- High-Performance Computing (80)
- Hydropower (11)
- Irradiation (3)
- Isotopes (46)
- ITER (7)
- Machine Learning (43)
- Materials (138)
- Materials Science (130)
- Mathematics (6)
- Mercury (12)
- Microelectronics (2)
- Microscopy (50)
- Molten Salt (8)
- Nanotechnology (60)
- National Security (54)
- Net Zero (10)
- Neutron Science (127)
- Nuclear Energy (101)
- Partnerships (37)
- Physics (58)
- Polymers (31)
- Quantum Computing (28)
- Quantum Science (65)
- Renewable Energy (2)
- Security (23)
- Simulation (42)
- Software (1)
- Space Exploration (24)
- Statistics (2)
- Summit (57)
- Sustainable Energy (115)
- Transformational Challenge Reactor (7)
- Transportation (92)
Media Contacts

As technology continues to evolve, cybersecurity threats do as well. To better safeguard digital information, a team of researchers at the US Department of Energy’s (DOE’s) Oak Ridge National Laboratory (ORNL) has developed Akatosh, a security analysis tool that works in conjunctio...
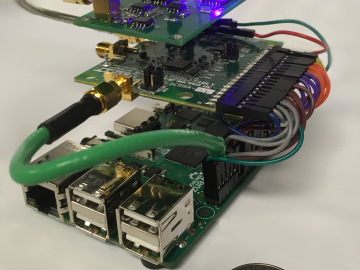
Qrypt, Inc., has exclusively licensed a novel cyber security technology from the Department of Energy’s Oak Ridge National Laboratory, promising a stronger defense against cyberattacks including those posed by quantum computing.

As leader of the RF, Communications, and Cyber-Physical Security Group at Oak Ridge National Laboratory, Kerekes heads an accelerated lab-directed research program to build virtual models of critical infrastructure systems like the power grid that can be used to develop ways to detect and repel cyber-intrusion and to make the network resilient when disruption occurs.

A new Oak Ridge National Laboratory-developed method promises to protect connected and autonomous vehicles from possible network intrusion. Researchers built a prototype plug-in device designed to alert drivers of vehicle cyberattacks. The prototype is coded to learn regular timing...

Virginia-based Lenvio Inc. has exclusively licensed a cyber security technology from the Department of Energy’s Oak Ridge National Laboratory that can quickly detect malicious behavior in software not previously identified as a threat.




