
Filter News
Area of Research
- Advanced Manufacturing (7)
- Biology and Environment (60)
- Biology and Soft Matter (1)
- Clean Energy (133)
- Climate and Environmental Systems (2)
- Computational Engineering (1)
- Computer Science (4)
- Electricity and Smart Grid (1)
- Functional Materials for Energy (1)
- Fusion and Fission (8)
- Fusion Energy (3)
- Isotope Development and Production (1)
- Isotopes (26)
- Materials (109)
- Materials Characterization (1)
- Materials for Computing (20)
- Materials Under Extremes (1)
- Mathematics (1)
- National Security (27)
- Neutron Science (37)
- Nuclear Science and Technology (11)
- Quantum information Science (9)
- Supercomputing (87)
- Transportation Systems (2)
News Topics
- (-) Climate Change (99)
- (-) Cybersecurity (35)
- (-) Decarbonization (79)
- (-) Frontier (42)
- (-) Isotopes (53)
- (-) Materials Science (139)
- (-) Quantum Science (69)
- (-) Space Exploration (25)
- (-) Transportation (97)
- 3-D Printing/Advanced Manufacturing (119)
- Advanced Reactors (34)
- Artificial Intelligence (91)
- Big Data (53)
- Bioenergy (91)
- Biology (98)
- Biomedical (58)
- Biotechnology (22)
- Buildings (57)
- Chemical Sciences (63)
- Clean Water (29)
- Composites (26)
- Computer Science (187)
- Coronavirus (46)
- Critical Materials (25)
- Education (4)
- Element Discovery (1)
- Emergency (2)
- Energy Storage (108)
- Environment (194)
- Exascale Computing (37)
- Fossil Energy (5)
- Fusion (54)
- Grid (62)
- High-Performance Computing (84)
- Hydropower (11)
- Irradiation (3)
- ITER (7)
- Machine Learning (47)
- Materials (143)
- Mathematics (7)
- Mercury (12)
- Microelectronics (3)
- Microscopy (51)
- Molten Salt (8)
- Nanotechnology (60)
- National Security (61)
- Net Zero (13)
- Neutron Science (131)
- Nuclear Energy (107)
- Partnerships (43)
- Physics (61)
- Polymers (33)
- Quantum Computing (34)
- Renewable Energy (2)
- Security (24)
- Simulation (47)
- Software (1)
- Statistics (3)
- Summit (57)
- Sustainable Energy (125)
- Transformational Challenge Reactor (7)
Media Contacts
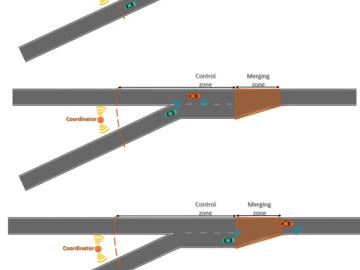
Self-driving cars promise to keep traffic moving smoothly and reduce fuel usage, but proving those advantages has been a challenge with so few connected and automated vehicles, or CAVs, currently on the road.
Physicists turned to the “doubly magic” tin isotope Sn-132, colliding it with a target at Oak Ridge National Laboratory to assess its properties as it lost a neutron to become Sn-131.
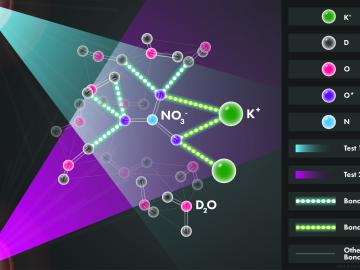
Scientists at the Department of Energy’s Oak Ridge National Laboratory used neutrons, isotopes and simulations to “see” the atomic structure of a saturated solution and found evidence supporting one of two competing hypotheses about how ions come

Long-haul tractor trailers, often referred to as “18-wheelers,” transport everything from household goods to supermarket foodstuffs across the United States every year. According to the Bureau of Transportation Statistics, these trucks moved more than 10 billion tons of goods—70.6 ...

As technology continues to evolve, cybersecurity threats do as well. To better safeguard digital information, a team of researchers at the US Department of Energy’s (DOE’s) Oak Ridge National Laboratory (ORNL) has developed Akatosh, a security analysis tool that works in conjunctio...
Qrypt, Inc., has exclusively licensed a novel cyber security technology from the Department of Energy’s Oak Ridge National Laboratory, promising a stronger defense against cyberattacks including those posed by quantum computing.
Sergei Kalinin of the Department of Energy’s Oak Ridge National Laboratory knows that seeing something is not the same as understanding it. As director of ORNL’s Institute for Functional Imaging of Materials, he convenes experts in microscopy and computing to gain scientific insigh...

The materials inside a fusion reactor must withstand one of the most extreme environments in science, with temperatures in the thousands of degrees Celsius and a constant bombardment of neutron radiation and deuterium and tritium, isotopes of hydrogen, from the volatile plasma at th...

Oak Ridge National Laboratory scientists have improved a mixture of materials used to 3D print permanent magnets with increased density, which could yield longer lasting, better performing magnets for electric motors, sensors and vehicle applications. Building on previous research, ...

As leader of the RF, Communications, and Cyber-Physical Security Group at Oak Ridge National Laboratory, Kerekes heads an accelerated lab-directed research program to build virtual models of critical infrastructure systems like the power grid that can be used to develop ways to detect and repel cyber-intrusion and to make the network resilient when disruption occurs.


