Topic:
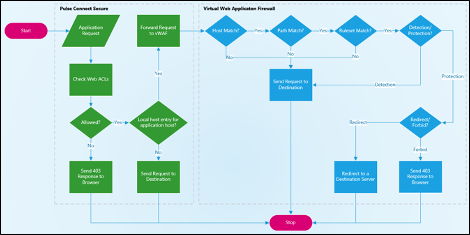
Application request flow through protected PCS and vWAF configurations.
An XSS attack leverages the ability of a malicious actor to submit data or commands through user input forms or through client-side manipulation of the URL. These attacks can cause temporary or long-term effects and can retrieve sensitive data from any targeted backend system or victim’s browser. The built-in features of the vWAF protects websites from known XSS attacks, while the local host configuration capabilities of PCS control redirection of traffic through the vWAF and decoupling of the PCS and vWAF configurations. Complimenting these capabilities are the unique, application-specific FQDNs that yield fine-grained control at the application level.
Media Contact
Scott Jones
, Communications Manager, Computing and Computational Sciences Directorate
, 865.241.6491
|
JONESG@ORNL.GOV


